‘WannaCry hacker group’ Email Scam is a new bitcoin email scam that is carried out by means of mass mailing of emails. In these email letters, scammers calling themselves ‘WannaCry hacker group’ inform the recipient that his email account was hacked, cybercriminals were able to infect the user’s device with a virus, and besides, they got access to all his emails and instant messengers. To attract maximum attention, the recipient password has been added to the header of the letters, the same password is also given in the text of the email letters.
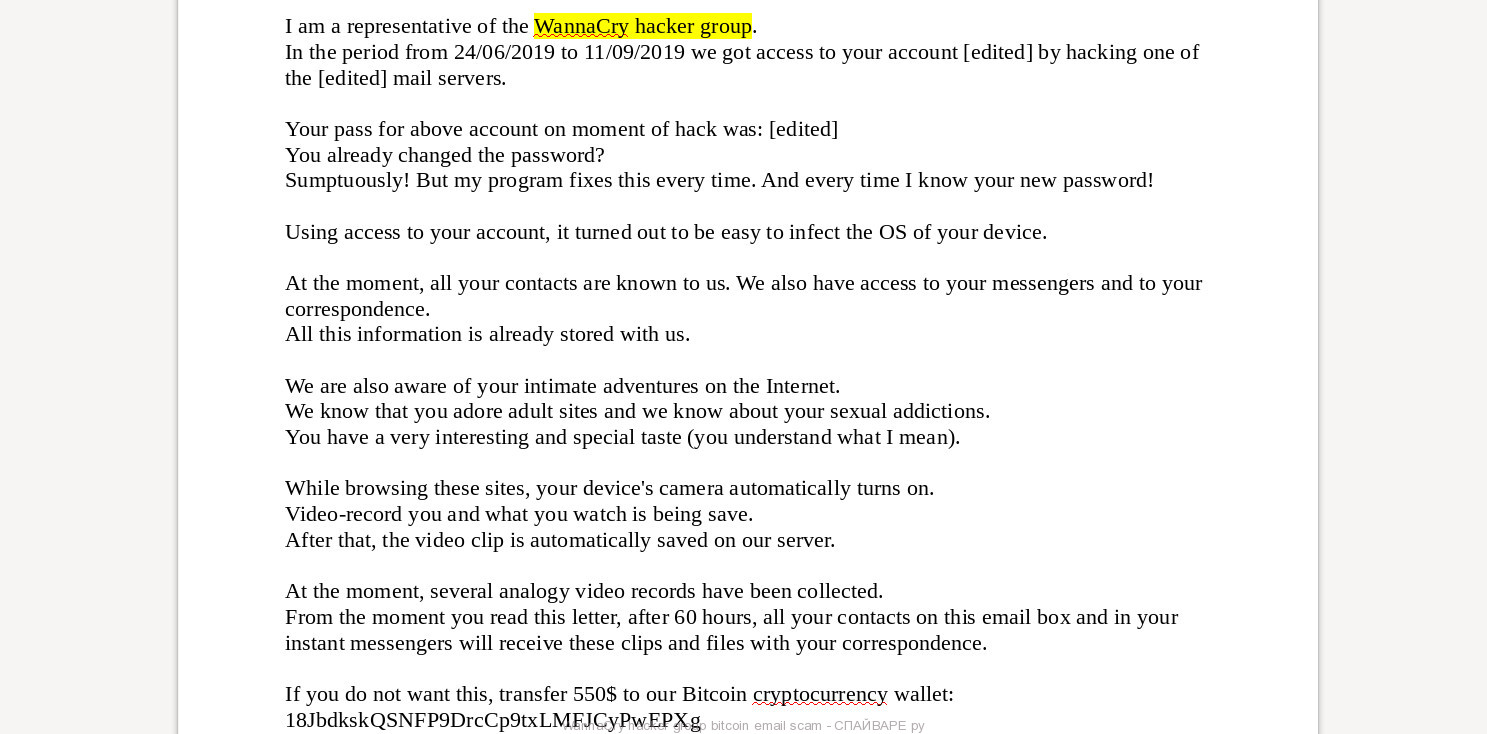
‘WannaCry hacker group’ bitcoin email scam
This email scam has at least two modifications. In the first case, email letters were sent from the ‘ChaosCC hacker group’, in the second, scammers used the ‘WannaCry hacker group’. In both cases, the sender addresses were created automatically from the list of websites that have a different subject and geographical location. To confirm the fact of hacking, the user’s password is included in the text of the email letter. The scammers report that they were able to make a video using the device’s webcam, which shows how the recipient of the email browses sites with pornographic content. Cybercriminals threaten that this record will be sent to friends and colleagues of the recipient, 60 hours after reading the letter. If the recipient does not want this to happen, he must send the ransom to the Bitcoin scam wallet.
An example of the text that is given in the email letter:
Hello!
I am a representative of the WannaCry hacker group.
In the period from 24/06/2019 to 11/09/2019 we got access to your account [removed] by hacking one of the [removed] mail servers.Your pass for above account on moment of hack was: [removed] You already changed the password?
Sumptuously! But my program fixes this every time. And every time I know your new password!Using access to your account, it turned out to be easy to infect the OS of your device.
At the moment, all your contacts are known to us. We also have access to your messengers and to your correspondence.
All this information is already stored with us.We are also aware of your intimate adventures on the Internet.
We know that you adore adult sites and we know about your sexual addictions.
You have a very interesting and special taste (you understand what I mean).While browsing these sites, your device’s camera automatically turns on.
Video-record you and what you watch is being save.
After that, the video clip is automatically saved on our server.At the moment, several analogy video records have been collected.
From the moment you read this letter, after 60 hours, all your contacts on this email box and in your instant messengers will receive these clips and files with your correspondence.If you do not want this, transfer 550$ to our Bitcoin cryptocurrency wallet: 18JbdkskQSNFP9DrcCp9txLMFJCyPwEPXg
I guarantee that we will then destroy all your secrets!As soon as the money is in our account — your data will be immediately destroyed!
If no money arrives, files with video and correspondence will be sent to all your contacts.You decide… Pay or live in hell out of shame…
We believe that this whole story will teach you how to use gadgets properly!
Everyone loves adult sites, you’re just out of luck.
For the future — just cover a sticker your device’s camera when you visit adult sites!Take care of yourself!
There were already a lot of similar spam emails with threats to the recipient and ransom demands. Its main difference is that cyber criminals posing as a group associated with developers ‘WannaCry’ virus. In this way, they want to make their threats more real and effective. Our team examined several samples of these email letters and compared them (with the sender’s name ‘WannaCry hacker group’ and ‘ChaosCC hacker group’). There is practically no difference between them. The passwords that are present in the emails are real. But, all these passwords were used by users quite a few years ago (10 or more). Therefore, we can conclude that fraudsters used user data that was stolen for a long time ago.
Experts confirm that such email letters are not individual messages, but mass spam mailing. Fraudsters do not have any information that could compromise the recipient of the email. With the help of social engineering, cybercriminals try to scare the recipient of the letter and force him to pay a ransom to an anonymous bitcoin wallet. Currently, we see that such email letters continue to be sent, they have slightly different text (for bypassing spam filters) and a new bitcoin wallet.
Threat Summary
| Name | WannaCry hacker group Email Scam |
| Type | Bitcoin Email Scam, Sextortion, Phishing |
| Sender | WannaCry hacker group |
| Ransom amount | $550 |
| Distribution method | spam email campaigns |
| Protection/Removal | How to protect yourself from WannaCry hacker group email scam |
What to do when receiving WannaCry hacker group email scam
We advise you to ignore such email letters and not trust the information that they provide. If you, your friends or relatives received a letter from so called ‘WannaCry hacker group’, then follow these simple steps below:
- Do not pay the ransom
- If the password provided in the letter is still used by you, then you must urgently change it
- If there is a link in the text of the letter or a file is attached to the letter, do not open this file
- Mark this email as SPAM, then delete it
- If you suspect that the computer is infected with a trojan or other malware, then check the computer by performing a full scan
- Start using a program that blocks spam, phishing, and malicious sites.
How to scan your computer for malware
To find and remove malware, including trojans and spyware, you need to use special programs. First of all, of course, you must have an antivirus, but in addition to it, experts advise you to use special utilities that are designed specifically to search for and remove malware (adware viruses, trojans and spyware). One such program is Zemana Anti-malware. With it, you can check your computer and if you find malware, you can remove it for free.
Download Zemana AntiMalware using the following link and save the file to your desktop.
Run the program and, following the prompts of the Installation Wizard, install it on your computer. When the installation of Zemana Anti-Malware is completed, you will see the main program window.
Click the “Scan” button and wait for the scan to complete. Click “Next” to remove the found malware and move it to quarantine.
Finish words
If you or your friends received an email message from the ‘WannaCry hacker group’, please tell us and our readers about it.