Seto virus is a new ransomware. It is created to encrypt files on the computer. All encrypted files become useless and get the .seto file extension. Each folder containing the affected files contains a message informing the user about the presence of a malicious virus on the computer and its destructive impact on the target files.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-yKBR9rlo6R
or
https://gofile.io/?c=blfjRd
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gerentoshelp@firemail.ccYour personal ID:
0159###########################################
Seto ransomware virus is able to encrypt files such as movies, photos, documents, drawings, databases including common as:
.xpm, .wbmp, .bar, .xlgc, .accdb, .m3u, .mdb, .lvl, .slm, .xbdoc, .itl, .csv, .odp, .xyp, .1st, .docm, .xld, .xwp, .snx, .wp6, .ai, .hkx, .mpqge, .txt, .raf, .wm, .zip, .y, .ybk, .w3x, .odt, .tax, .wpg, .xx, .wri, .ncf, .xmind, .arch00, .wire, .r3d, .wotreplay, .pptm, .d3dbsp, .tor, .rb, .db0, .zdb, .png, .zw, .t12, .psd, .wpd, .odc, .sav, .ltx, .bc6, .cdr, .bc7, .wp4, .0, .xyw, .p12, .xlsb, .lrf, .lbf, .rar, .wav, .wpl, .xlsx, .p7c, .sr2, .js, .wmv, .kdc, .hvpl, .x3f, .xf, .mp4, .qdf, .dbf, .upk, .bkf, .odm, .hkdb, wallet, .wsd, .gdb, .kf, .vpk, .dcr, .wp5, .wpa, .zip, .cas, .wbm, .zif, .webp, .epk, .xlsm, .xlsx, .pst, .wbd, .wdp, .syncdb, .desc, .apk, .xbplate, .wmf, .mef, .pdf, .wpt, .vpp_pc, .fpk, .pem, .wmv, .xar, .xlsm, .srw, .sql, .wp, .1, .rwl, .wpd, .itdb, .rofl, .vtf, .dmp, .sie, .asset, .xxx, .flv, .wcf, .mcmeta, .xls, .wsc, .sum, .vdf, .ztmp, .ibank, .mrwref, .zdc, .2bp, .wma, .mlx, .wps, .iwd, .crw, .sidn, .t13, .dwg, .ysp, .wmo, .menu, .cfr, .wot, .xll, .cr2, .layout, .xdl, .wb2, .wma, .rw2, .pak, .bay, .pptx, .ntl, .hplg, .bkp, .mdbackup, .xls, .fsh, .indd, .sid, .x3d, .wgz, .webdoc, .pef, .3dm, .mov, .z3d, .nrw, .docx, .jpeg, .xy3, .blob, .vfs0, .orf, .psk, .dng, .pkpass, .wbk, .m4a, .wps, .doc, .gho, .rtf, .litemod, .xdb, .wdb, .arw, .cer, .dxg, .xmmap, .zi, .wmd, .raw, .py, .x3f, .m2, .sidd, .iwi, .jpe, .crt, .ws, .x, .xlk, .wpb, .esm, .map, .ff, .fos, .avi, .das, .yal, .3ds, .mddata, .7z, .svg, .big, .wn, .rgss3a
Attackers clearly inform each victim that he has the ability to recover locked files only paying a $980 ransom. After transferring the specified amount to cyber frauds, the user will receive a code key from them, which will help to decrypt and restore files affected by the Seto ransomware. If the money for the purchase of a unique tool for decrypting files will be transferred to the fraudsters within 72 hours, they are ready to give the victim a discount of 50%.
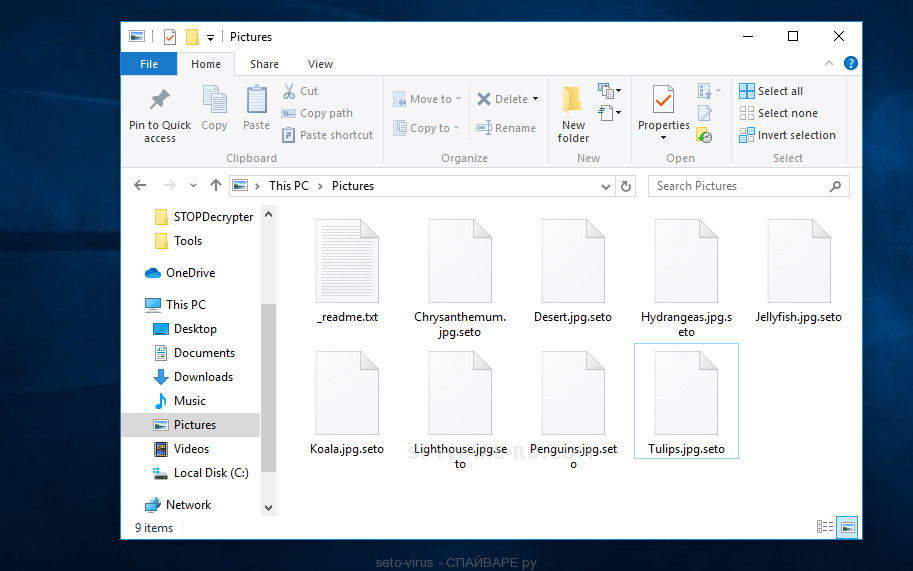
seto virus
Summary
| Name | Seto ransomware |
| Type | Ransomware, Crypto virus, File virus |
| Encrypted files extension | .Seto |
| Ransom note | _readme.txt |
| Contact | gerentoshelp@firemail.cc, gorentos@bitmessage.ch |
| Ransom amount | $980, $490 in Bitcoins |
| Distribution methods | Spam mails, Exploit kits, Social media, Torrent web-sites. |
| Removal | Seto virus removal guide |
On current time, there is no other way to unlock the affected files, but only to pay the ransom to cybercriminals. Developers of programs that can unlock these files are working on creating them, but the result is not yet, and it is not known when it will be. However, the user who will pay the ransom to the attackers cannot be completely sure of obtaining a unique code key, because he is dealing with unscrupulous and dishonest people who are ready to commit any immoral actions, including hiding after receiving the ransom from the victim, and not providing a tool to unlock the files.
Update: In some cases, you can recover files encrypted by Seto crypto virus using ShadowExplorer and PhotoRec. An example of recovering encrypted .seto files giveh here.
How to Remove Seto file virus (ransomware removal guide)
If you don’t have much experience in setting up and configuring the Windows operating system, then the best way to locate and remove Seto ransomware virus is to use malware removal tools which are listed below.
Zemana AntiMalware (ZAM) is full featured ransomware removal tool. It can help to delete Seto ransomware virus and other security threats. It uses 1% of your PC system resources. This tool has got simple and beautiful interface.
- First, click the following link, then click the ‘Download’ button in order to download the latest version of Zemana Anti Malware (ZAM).
Zemana Anti Malware download - At the download page, click on the Download button. Your browser will open the “Save as” prompt. Please save it onto your Windows desktop.
- After downloading is done, please close all software and open windows on your computer. Next, start a file called Zemana.AntiMalware.Setup.
- This will run the “Setup wizard” of Zemana Free onto your PC system. Follow the prompts and do not make any changes to default settings.
- When the Setup wizard has finished installing, the Zemana will run and open the main window.
- Further, click the “Scan” button . Zemana Anti-Malware application will scan through the whole system for Seto file virus. While the Zemana utility is checking, you may see number of objects it has identified as being infected by malicious software.
- Once the scan get finished, Zemana AntiMalware (ZAM) will show a scan report.
- In order to remove all items, simply press the “Next” button. The tool will delete ransomware virus and move all security threats to the program’s quarantine. Once finished, you may be prompted to restart the system.