‘Open .Kvag file‘ is a problem that you have encountered. To solve it, you first need to find out what Kvag files are. I’m sorry that I brought you bad news, but it’s impossible to open these files! Even if you rename them, delete the new extension or replace it, all the same, these files will not open. There is only one reason for this – a computer virus, which belongs to the ransomware group. All files with .Kvag extension are files that have been encrypted by the virus.
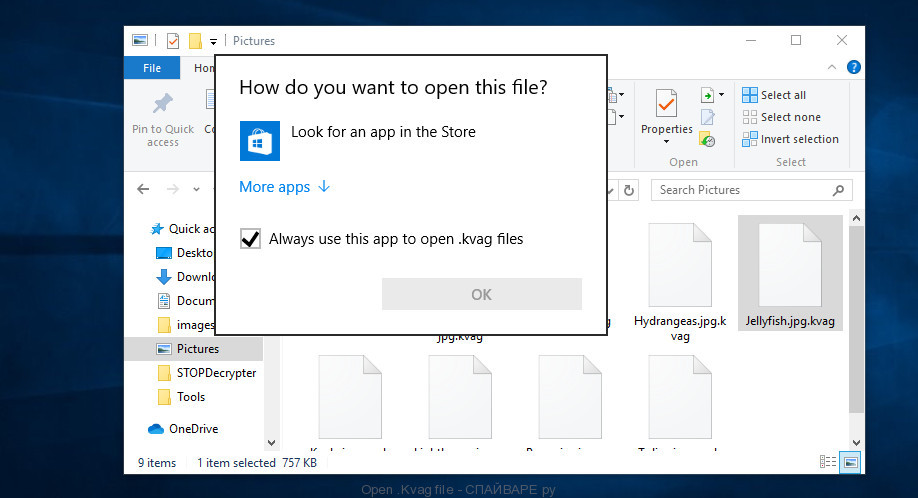
There is no way to open .Kvag files using the standard features of the Windows OS, when you try to open such files, the OS displays a message: ”How do you want to open this file?
To understand why your files suddenly stopped opening, you first need to find out what a ransomware is. Ransomware is a malicious software that is created by cybercriminals to encrypt files on a computer. The only way to unlock encrypted files is to pay a ransom. You must now understand that you are a victim of ransomware virus attack. There are various ways for your computer to become infected with with ransomware. Typically, computer can become infected when installing programs downloaded from various suspicious sites offering to download hacked software, key generators for paid programs, and so on. After the virus is launched, it starts the file encryption process. The ransomware tries to encrypt all available files, even those located on external and network drives. The virus can encrypt files of various types, including such as:
.xlsx, .wbd, .dbf, .iwd, .das, .wmd, .xlk, .odb, .syncdb, .ws, .xbplate, .bkf, .zw, .x3f, .wpa, .raw, .wpb, .xlgc, .dng, .mlx, .webdoc, .qdf, .sr2, .ppt, .xml, .rofl, .css, .3ds, .vdf, .3dm, .mdbackup, .upk, .wbk, .srw, .vpk, .m3u, .pdf, .asset, .ybk, .zi, .wot, .wmo, wallet, .sid, .zif, .itl, .zip, .menu, .gdb, .wpe, .wp7, .rgss3a, .ai, .dmp, .dazip, .rb, .xpm, .wgz, .wbm, .map, .mef, .kf, .vtf, .accdb, .z, .mpqge, .py, .wsd, .x, .odp, .desc, .jpe, .wmf, .bkp, .wp6, .wbz, .wpd, .d3dbsp, .tax, .erf, .ibank, .layout, .mcmeta, .csv, .crt, .wp, .cas, .wma, .zip, .db0, .wn, .cer, .vfs0, .cr2, .dcr, .xx, .7z, .docx, .hvpl, .esm, .wdb, .raf, .sie, .xf, .wpt, .sum, .mdb, .xlsm, .arch00, .xwp, .mp4, .wbmp, .z3d, .xmmap, .wmv, .hkx, .wbc, .svg, .rwl, .m4a, .wb2, .sb, .xls, .sidn, .w3x, .p7c, .p12, .zdc, .der, .ntl, .1, .eps, .bay, .bar, .yal, .2bp, .wire, .sql, .mrwref, .m2, .crw, .wpl, .sav, .gho, .wps, .xdl, .pptx, .lrf, .zdb, .p7b, .ods, .xlsm, .yml, .qic, .snx, .pdd, .xld, .psk, .mddata, .epk, .re4, .ltx, .psd, .vpp_pc, .big, .xlsb, .dwg, .dba, .js, .ysp, .doc, .xdb, .orf, .rim, .icxs, .rtf, .pak, .ztmp, .mdf, .pem, .avi, .pef, .wdp, .bsa, .wpg, .xlsx, .x3d, .sidd, .lbf, .forge, .wp4, .odm, .bik, .iwi, .wcf, .rw2, .wpw, .wotreplay, .ptx, .fos, .lvl, .webp, .kdb, .wmv, .fsh, .arw, .t12, .nrw, .rar, .xyw, .pkpass, .hplg, .flv, .odt, .y, .wsh, .itdb, .jpg, .vcf, .blob, .wp5, .cdr, .xyp, .jpeg, .xy3, .xbdoc, .png, .1st, .xmind, .3fr, .kdc, .x3f, .wpd, .odc, .srf, .litemod, .pst, .bc6, .wav, .ff, .docm
In all directories where there are encrypted files, the virus creates a new file called ‘_readme.txt’. In that file, criminals report that all files on the computer are encrypted, and the only way to recover documents, photos and other files is to pay a ransom. Below is an example of ransom note delivered by Kvag virus:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-JbqssVgS78
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gerentoshelp@firemail.cc
Thus, the only way to open files is to decrypt them. At the moment, only criminals can decrypt all encrypted files. The reason for this is that the virus use a very strong encryption system, which blocks the ability to find the decryption key. Despite this, our team has developed several ways that can allow you to return files. These methods do not require paid programs and special knowledge.
Threat Summary
| Name | Kvag virus |
| Type | File locker, Ransomware, Crypto virus, Crypto malware, Filecoder |
| Encrypted files extension | .kvag |
| Contact | gorentos@bitmessage.ch, gerentoshelp@firemail.cc |
| Ransom note | _readme.txt |
| Ransom amount | $980 in Bitcoins |
| Symptoms | Encrypted photos, documents and music. Windows Explorer displays a blank icon for the file type. Your file directories contain a ‘ransom note’ file. |
| Distribution methods | Malicious email attachments. Exploit kits (cybercriminals use ransomware packaged in an ‘exploit kit’ that can find a vulnerability in PDF reader, MS Windows OS, Internet browser, Adobe Flash Player). Social media posts (they can be used to force users to download malware with a built-in ransomware downloader or click a malicious link). Remote desktop protocol (RDP) hacking. |
Quick links
How to remove Kvag virus (ransomware removal guide)
Attention! Before you start recovering files after ransomware virus attack, you should check your computer for malware. We recommend that you do not just re-scan your computer with antivirus software (if you have one, if you don’t have one, you must install it), but use malware removal utilities that are designed to search for malicious software (ransomware, spyware, trojans, adware, and so on). You can use the programs below:
Zemana AntiMalware (ZAM) is full featured ransomware removal tool. It can help to delete Kvag ransomware virus and other security threats. It uses 1% of your PC system resources. This tool has got simple and beautiful interface.
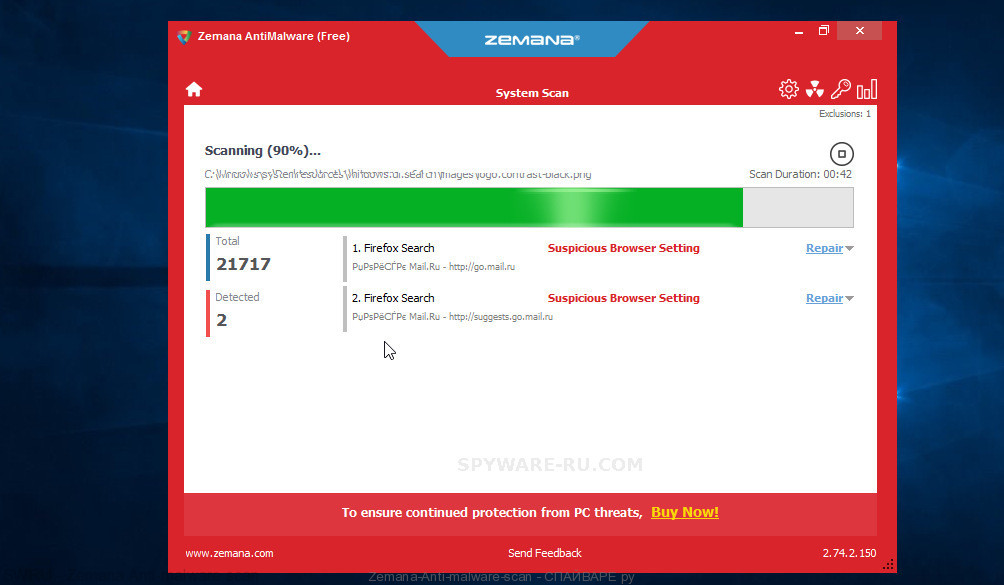
To find and remove Kvag virus, follow these few simple steps below:
- Download Zemana Anti Malware (ZAM) from the link below.
Zemana Anti Malware download - At the download page, click on the Download button..
- Close all open windows and start a file called Zemana.AntiMalware.Setup.
- Follow the prompts and do not make any changes to default settings.
- When the Setup wizard has finished installing, the Zemana will run and open the main window.
- Click the “Scan” button, once the scan get finished, Zemana AntiMalware (ZAM) will show a scan report.
- In order to remove all items, simply press the “Next” button.
How to restore .kvag files (without decryption)
Despite the fact that it is impossible to decrypt .kvag files without a key, you have the opportunity to restore your files. Below in this article we will give several ways, please try all of them. Perhaps one of them will allow you to completely restore the files, or rather, return them to their original state, to the state that was before their encryption.
At this stage, I want to emphasize that before recovering files, you must definitely check your computer for viruses, find and remove malware that encrypted your files. The only way to skip this step is to get the disk with encrypted files and connect it to another computer, then use it to restore your files. Attention, using a disk on another computer, there is a small chance that you accidentally infect that computer with this virus.
How to restore .kvag files using ShadowExplorer
To restore documents, photos, databases and other important files, that is, practically “decrypt .kvag files without a key,” we first recommend using a free program called ShadowExplorer. If you have not come across this program, then here is some information about it. It is a small utility that allows you to easily access copies of files that are created automatically by a standard OS function called Windows Previous Versions.
Download the program using the link that you can find below. We recommend that you save the downloaded file to your desktop, so you can easily find it after the download is complete.
When the program download is complete, you will see a file called ShadowExplorer-0.9-portable.zip. The utility is in the archive, so you need to unzip the archive before starting the program. Right-click on this file and select the option called Extract All. Now open folder ShadowExplorerPortable.
In the list of files, find the ShadowExplorerPortable program and run it.
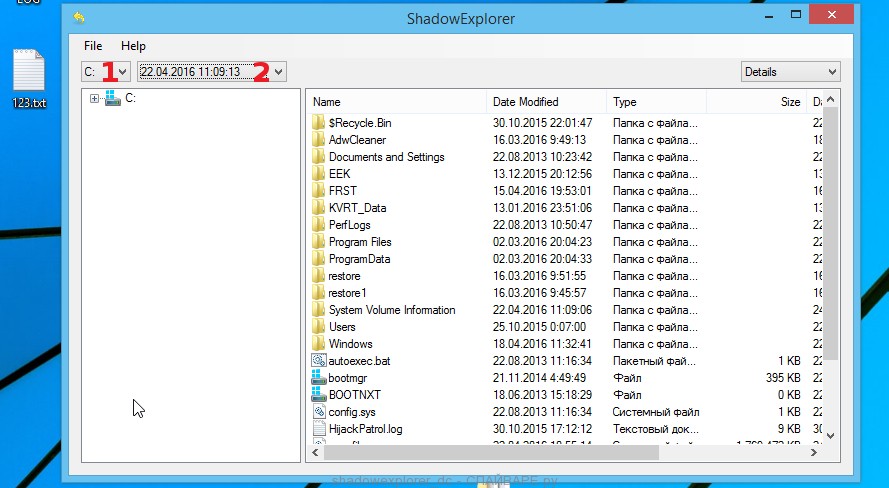
The main program window will open before you, as in the following example. The main window is divided into two parts – left and right. In the left part of the window, select the drive on which the encrypted files are located and select the date closest to the moment when the virus attacks your computer, encrypts the files and has changed the file extension to .kvag. In the right part of the window, select the file you want to restore, then right-click on it.
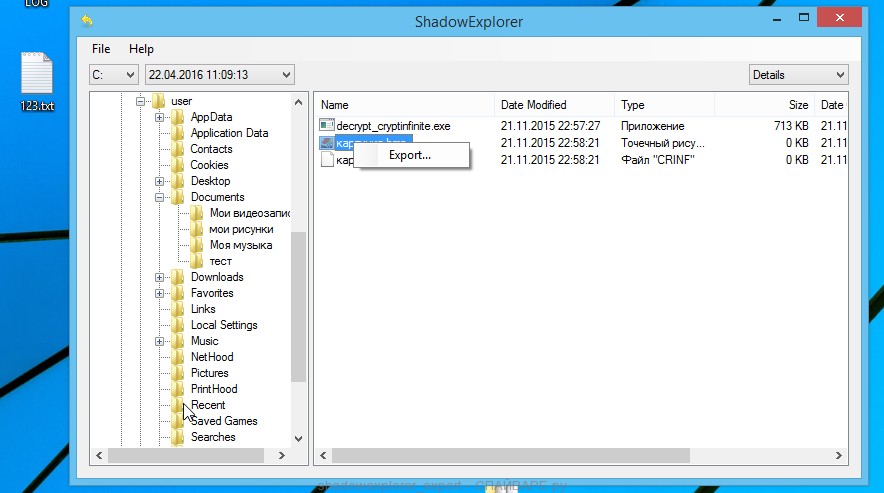
A small pop-up menu will open before you, select Export in it. In the next window, select the directory where the recovered files will be saved.
What else do I want to say about the process of recovering encrypted files using the ShadowExplorer tool. Unfortunately, very often ransomware disable the Windows Previous Versions function and delete all saved copies of files. Therefore, after starting the ShadowExplorer, you may find that it is impossible to recover files. In this case, use another method of recovering encrypted .kvag files, which is given below.
How to restore .kvag files using PhotoRec
Another way to recover encrypted .kvag files is the ability to use utilities designed to find and recover accidentally deleted and lost data. We recommend that you use the free PhotoRec tool. It is one of the best and has already helped readers of our site repeatedly recover encrypted files in a seemingly absolutely hopeless situation.
Before using the program, you need to download it. Use the link below.
When the file is downloaded, in the folder where you saved it you will see a file with the name ‘testdisk-7.0.win_.zip’. This file is the archive that contains the PhotoRec. To use the PhotoRec, this archive must be unzipped. Right-click on the file and select the item called Extract All. Open the folder with the name testdisk-7.0, you will see a list of files similar to the one below.
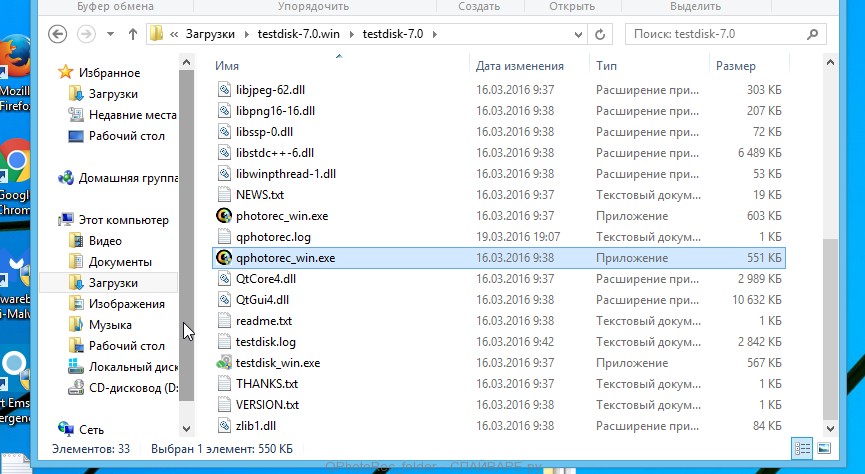
In the contents of the directory that opens, find the file with the name QPhotoRec_Win and run it. You will be shown a window similar to the one in the following figure. This is the main PhotoRec window.
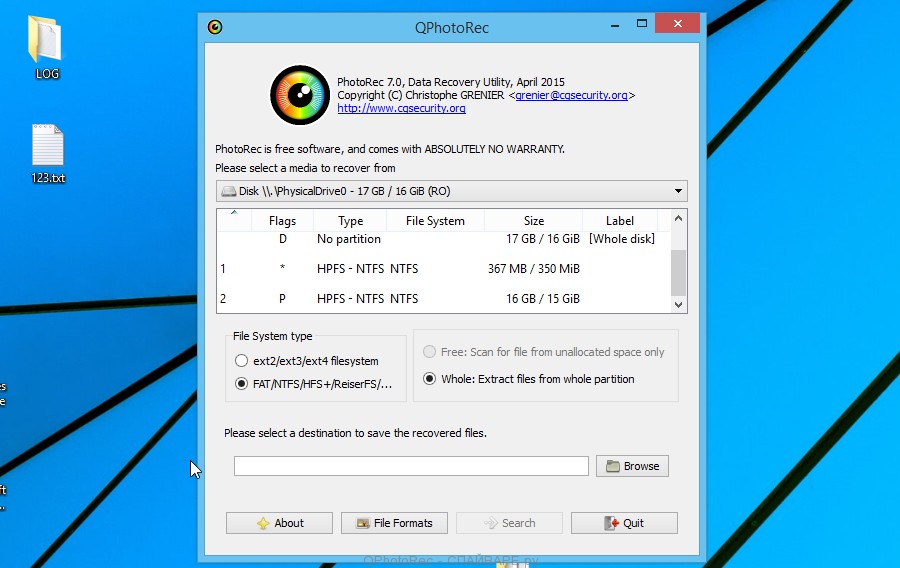
Here you need to select the physical disk and the disk partition (disk name) where the encrypted .kvag files are located. Note that in section ‘File System Type’, option ‘FAT/NTFS’ must be selected. Now select the folder where the recovered files will be written. We recommend using a partition or drive that does not contain encrypted files. It is better to use external media. It is very important! Since the PhotoRec restores files that were deleted by the Windows OS, if you restore them to the same drive on which you are trying to find them, a situation may occur when the Windows simply physically overwrites them and you can no longer recover such files.
Next, at the bottom of the window, click File Formats. A small window opens that lists the types of files that the PhotoRec can find and restore.
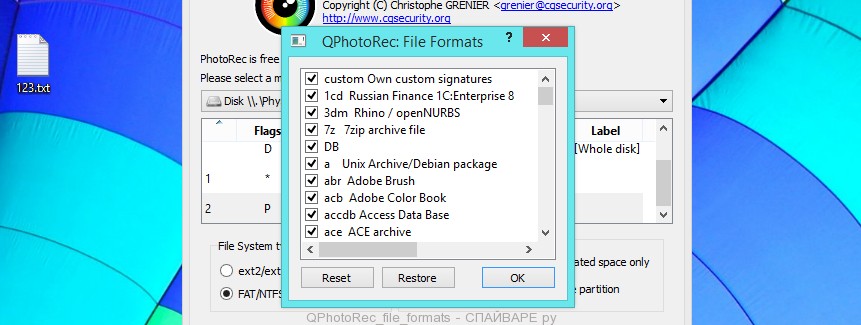
Leave only those file types that you need to recover selected. For example, if you want to restore images of ‘jpg’ format, then select the file type ‘jpg’. Having decided which files to recover, click OK button.
Having completed the steps listed above, you have made all the settings necessary to search and restore encrypted .kvag files. It remains only to click on the Search button. The process of searching and restoring files can take a very long time, be sure not to turn off the computer or restart it. During this process, the program will show the current search location (disk sector), how many and which files were found and restored.
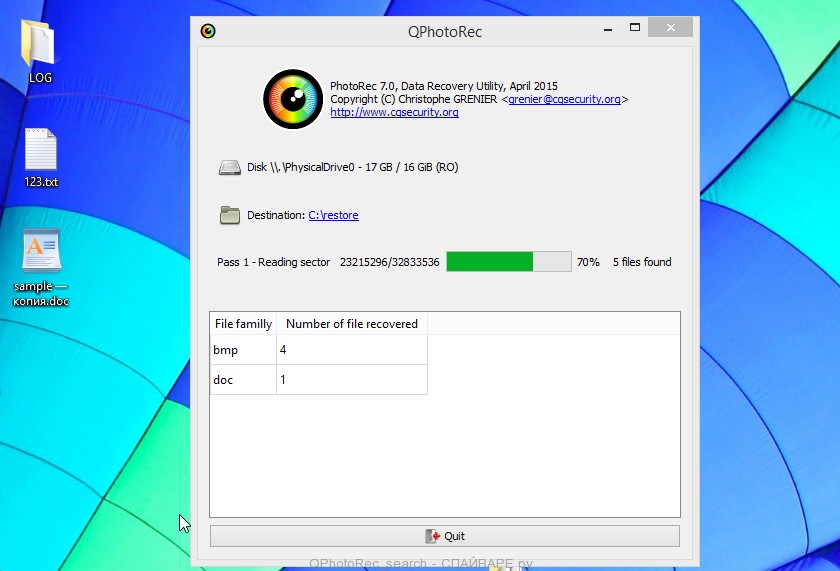
When the file recovery process is complete, click the Quit button. Then open the directory that you previously selected as the place where the recovered files will be written.
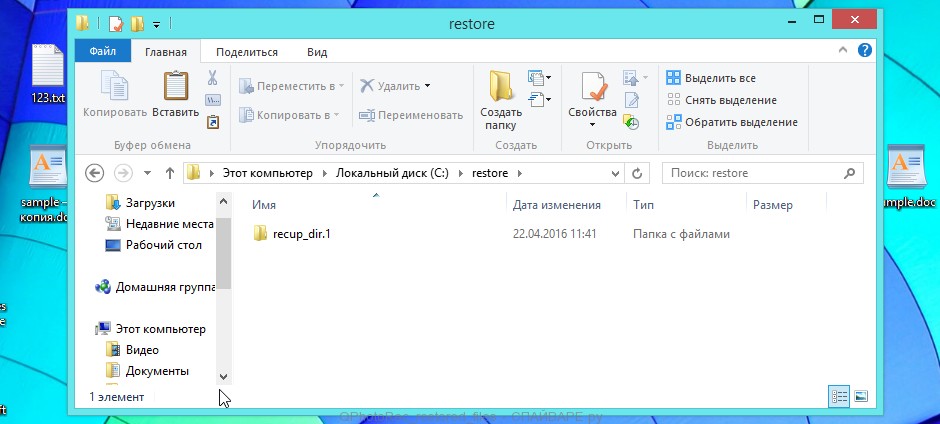
Here you will see one or more directories with the name recup_dir (recup_dir.1, recup_dir.2, …). Check these folder to find the files you need. The file name may not be restored, so to find what you need, use file sorting, as well as the standard Windows OS search by file contents.
I hope this information helped you remove Kvag virus and restore the encrypted files. If you have any questions or you have information that will help readers of this article, then please add your comment below.


Hi . How can I get rid of the file extension (.kvag). Because the above software only returns removable files
‘.kvag’ file extension is just a sign that the file is encrypted. By removing this extension, you will not decrypt the file. That is, even if you delete this extension, you still can not open the file.
Dear Admin,
i have some important data (documents) that have been encrypted as KVAG and locked. is there any possibility of getting them back ?
any decrypt tool come for .kvag extension.how to remove these virus
You can try to restore encrypted files using the steps described in this manual. Not so long ago, information appeared that in SOME CASES .kvag files can be decrypted. This is when the files were encrypted using an offline key. The virus uses an offline key when for some reason it cannot communicate with the control server. Read the answer given here. It concerns a virus using a different extension, but it will suit you too. You will need to use the following data:
—–BEGIN PRIVATE KEY—–
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQCT7/iU8i1IJPzZ
ACQS2Yl8s9/mberZDpRZu/7YmgSr+opyFtRtGOcBqbJeQyBbjUT6+MsJT6pCBwVR
68Rpgtu3X2xffTCJe0JPqitcIIgwdlNgJJsq++VYh1RqXqMGPZM657Doj9pfIvXY
BfWNb5KW3VyTM4G42j4T6B+lKxp5HVLqv2qYj7IVEiRfRVIVa7B7+dj5oE2BDU+4
qOzJFEjOUPwOIg3qZR1p6YeSk/dghgVYw8St4c7A4+uxfPGXkoHz3CwRY0DYCIAT
q5km6XSSdcIz6O44phXUDKIZ/81E3sv7j9Su6BbgS88YskA0TYXV33/P4ZsINI8B
5Q2fPhhjAgMBAAECggEAYp16AJf7dXcqkeEVKveWPemOHIYzIiQk4jh+ppbs/FOU
DH+JdXw/KY2cmFd4726ZiA9nETrozQDvG+/lS0xu+KsEjBbgzxS6XG6cXtpUzrFh
3NoqEZo/BSeZLxsM43ESfxbJiA20zOx6I1m9mV3Bww2m031nQPlCnnSC+9Bi4k6V
aOLIlvSznPJ+m1vgRR7PMz2Oj4YhfV/esDjp3f2bFQFz2Mxr4IOw5husSnQKIgjj
PGXbwIM64daGCT1G1E8VhEVHLsW6IeEsdO0fwwNj6YAoFyqky8p+YxzSgFY+NoB/
Bj/8UGVUkrblp/otGP2sU1t4lJm5GUmIKwFmLanakQKBgQDFC8Pee1JwYs/a7B+T
fplDUHOPKxHlM+xvi482T/n1+1QETH0ACzG4tn4NrNph5TV9w6R2MRkavonHXfok
XeT25d/qQNloCviBUpgourEk3m3Vb/O9TcWHlgP3eQzNM0nzmgGs97KYmrFL28cO
XGi+30F33SMjjmOFHhb9zaq5WQKBgQDAMtwPOXJs/Dc24Xfj6SETYQVNVYLFB9zZ
Hs+AvpebaCFewnsrdW7E20l5kYdHhYc32fsk/FX4c7h4CqpEeFyFE1MuAImDb9GI
aGIplP31j8IK4J60nY31s1jfblhL65f3KJjqmdLlMz9puY8fwMEfuPqDB0fz4XlR
0otXHANsGwKBgBFsZ+ZtWy3K3vxJssUVBbJZE87ODSgKPlbirUgtLDoe/h/fL5Jo
av4dTOoipbDQVrmHKiy1TLX7sS0q1yqODufyDammEFNN3Ql6Zy/6yh0reeTMoG3V
yaiikDk6v/IJHfnnXUyRHn619wVxKpnPfAecsCpMKIZFWfF0Zq4MmJMJAoGBAKCz
pdZA9VD1DgGgQgtZaSN38uP3hLDT4y/TmDKQqdjyFzzRJgVvWh/VLrksGk2N80Ka
y2fgaM2ljG8qk7VOYiWOw/Tp1BEHFM6WYMVd435IJjnMGEbymbj/rWacL83C/jxV
QI6f8Xtc/z+aPHaTR6cLlsKp+tqLA1KL1aAPNzlTAoGBAJBuE3+bUANOxkLpr1+v
7bk+Z61dNHmkvrjcA3g68/Xb/ZVEbbQYhNxJla+QVpaE/stGudT/3QXRx3faiZtQ
0EcMJBUQXuuUBKI+nKoL+/OXUJTjfXpMwVs7GrDQ5DEw09XZ9q6js1uarhwGId0d
qYnUx7uCbHFfG2gDOn2jS19P
—–END PRIVATE KEY—–
Personal ID:
9AGuZTsAcD5zyqTnBa8w6fa8SRmIGYbvxMuTLIt1
File name:
_readme.txt
More information here.
Before you try to decrypt .kvag files, we recommend that you make a backup copy of them.