Mogranos file virus is a new Ransomware. This dangerous program seals the files on the users’ computers. This restriction can be removed only if the user pays the hackers the required amount of money. If you came across this article, you were probably searching for other options on how to neutralize and remove Mogranos file virus, which does not involve paying the ransom. The goal of this article is to provide you with the necessary information that can help you understand how this program operates, defuse the infection and recover (decrypt) some of your files that have been sealed. The most important part of it is that you will be able to avoid unnecessary payments. Also following the steps that are listed below are not dangerous for your PC.
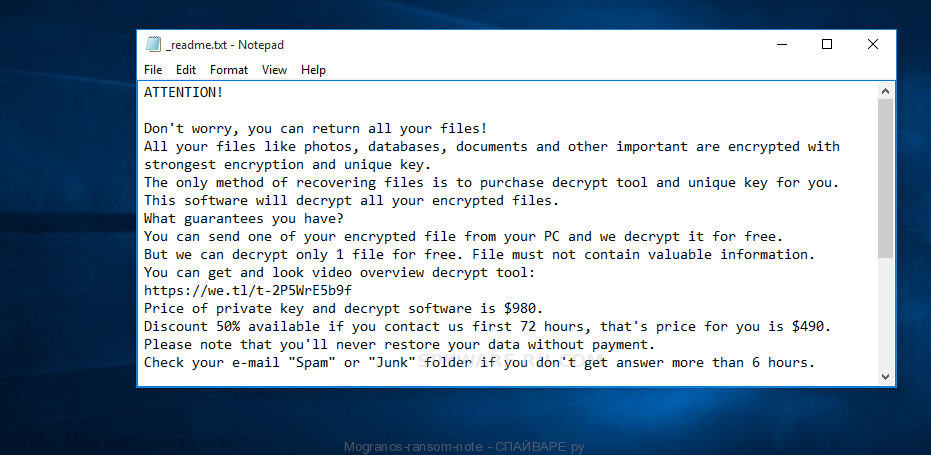
Mogranos ransom note
Mogranos file virus can encipher files, which are stored on the hard disk of the users’ devices. The information that is located there becomes totally unavailable for use. After the computer is infected and files are sealed, the hackers start to require users to pay the kind of a ransom to get their information unblocked. Often this ransom is not ordinary money because the hackers need this payment to be untraceable and they want to remain anonymous. That is why they demand users to pay the ransom in a virtual currency called BitCoins. It meets all the requirements. Moreover, the hackers insist that this is the only way to get desired but sealed files back.
Full text of the Mogranos file virus ransom note is:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-2P5WrE5b9f
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gorentos2@firemail.ccYour personal ID:
[Edited]
Mogranos file virus is a very treacherous malware; it applies a lot of transponders because it tries to occupy as many devices as it is possible. Some of the computers that use Microsoft Operation systems may have some weaknesses; also, some users are too careless about the security of their device when using the Internet. Ransomware uses these elements to infect the computer. Nevertheless, these ways of infecting are not the only ones. Your computer may be infected by opening an email from an unknown person, opening an unknown site or installing suspicious programs and updates. As you can see, there are a lot of ways to get your device occupied by ransomware viruses.
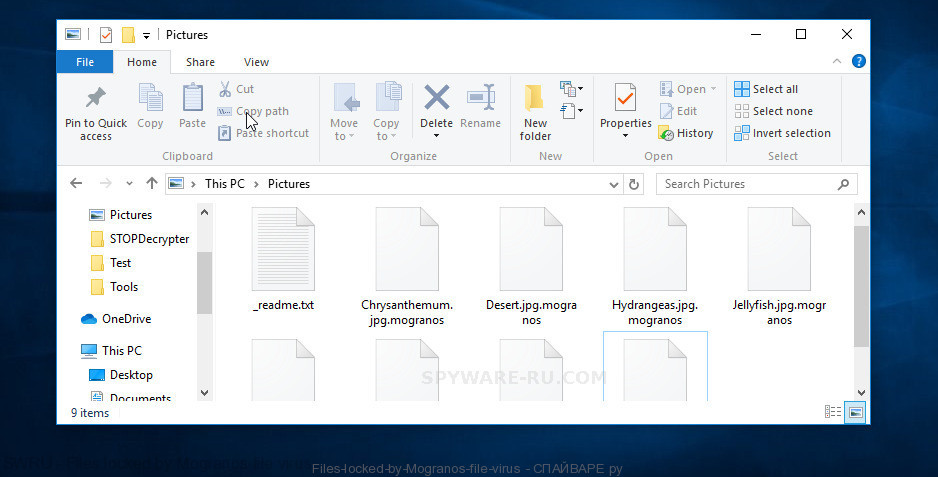
Files locked by Mogranos file virus
User does not have to do a lot to start the encryption process. Usually, it takes only a couple of clicks to get your device infected. It happens due to the fact that hackers tend to make this process as fast and as invisible as possible. Well, this process is really invisible if most antivirus software cannot detect it. Moreover, because antivirus programs cannot detect these viruses, they cannot provide proper protection for your computer. You will find out that your device was infected only when the message that demands the ransom appears.
The infected computer may start a real cyber epidemic. It requires only the connection to the local area network to contaminate more devices. The threat grows in geometrical progression because a lot of crypto viruses are able to spread themselves freely. That is the reason why you have to get your computer disconnected from the local area network if you think that your device has been infected.
SUMMARY
| Name | Mogranos |
| Type | Ransomware, Crypto virus, Crypto malware, File virus |
| Ransom note | _readme.txt |
| Encrypted files extension | .dalle |
| Ransom amount | $980 |
| Distribution methods | From phishing email scam that attempts to scare users into acting impulsively to Drive-by downloads from a compromised webpages and Social media, like web-based instant messaging programs. |
| Removal | Mogranos ransomware removal steps |
| Decryption | Mogranos file virus decryption steps |
We will be honest: treating this kind of virus is an incredibly complicated task. You will need to try very hard to get rid of this cybernetic threat. In addition, the process of treating depends on security policy. It is important if you update systems in time or check your antivirus software. It is also necessary to make a habit of making copies of important files and store them on an external storage device. Despite all the measures taken, it is necessary to understand what kind of malware you are dealing with. Each of these viruses requires a special approach. Only after that, you have to proceed to further action.
How to Remove Mogranos file virus (ransomware removal guide)
When a ransomware activity is suspected, it is recommended to full-scan your computer with anti malware tool. All malware removal programs mentioned below are third party tools which hold a good reputation in removing ransomware, trojans, spyware, worms and other malware.
MalwareBytes Anti-malware is a free downloadable malware removal tool that provides on-demand scanning and helps remove Mogranos file virus, ransomware, viruses, trojans, spyware, worms, and other malicious software. MalwareBytes offers a 14 day trial of their Premium edition. This Premium edition provides Real Time Protection and can act as a full anti-virus suite.
- MalwareBytes Anti Malware can be downloaded from the following link. Save it on your Desktop.
Malwarebytes Antimalware download link - At the download page, click on the Download button. Your web browser will open the “Save as” prompt. Please save it onto your Windows desktop.
- After the downloading process is done, please close all software and open windows on your personal computer. Double-click on the icon that’s called mb3-setup.
- This will open the “Setup wizard” of MalwareBytes AntiMalware (MBAM) onto your computer. Follow the prompts and do not make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes AntiMalware will launch and show the main window.
- Further, press the “Scan Now” button to find Mogranos crypto malware and other security threats. This process can take some time, so please be patient. While the MalwareBytes Anti Malware program is checking, you can see count of objects it has identified as threat.
- Once MalwareBytes completes the scan, MalwareBytes Anti-Malware (MBAM) will open a scan report.
- Review the results once the utility has finished the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply click the “Quarantine Selected” button. Once that process is finished, you may be prompted to restart the PC system.
- Close the AntiMalware and continue with the next step.
How to decrypt .Mogranos files (Mogranos decryption steps)
Experienced security professional Michael Gillespie has developed a free Mogranos Decryption tool that named STOP Decrypter. It might restore (decrypt) your files.
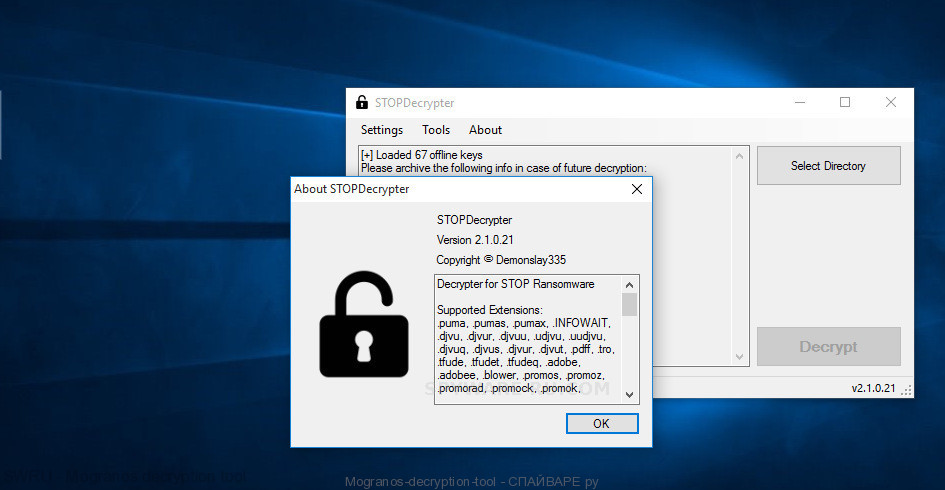
Mogranos decryption tool
You can download Mogranos Decryption tool from the link below.
https://download.bleepingcomputer.com/demonslay335/STOPDecrypter.zip