A ransomware called Karl file virus is new malicious software created by cybercriminal. The principle of its functioning and the method of distribution is the same as in the case of Domn virus and Kvag virus, the only difference is the Karl extension applied to the personal files that are encrypted with it.
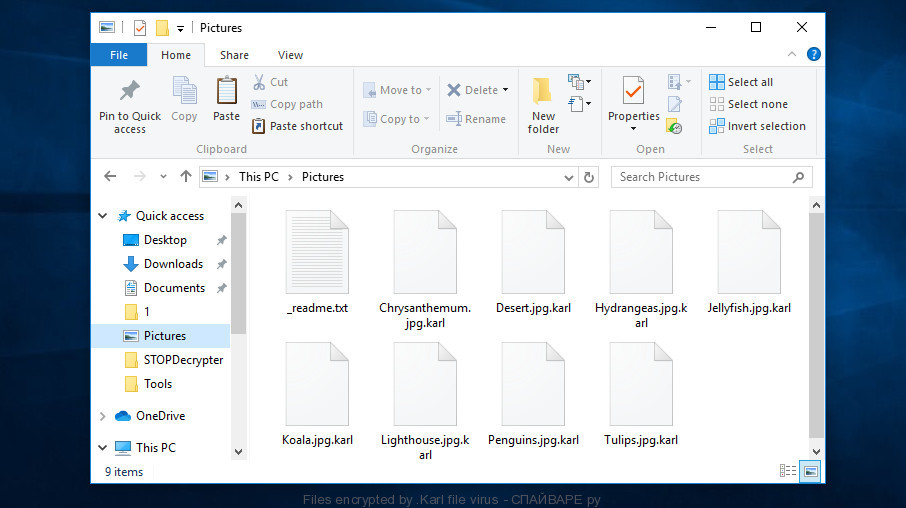
Files encrypted by .Karl file virus
Karl file virus is designed to secretly penetrate the computer in order to encrypt files like video materials, archives, web application-related files, photos, database, drawings and documents, by using a strong encryption method. In case of infection with this ransomware virus, the victim will not be able to decrypt files on his own, even by renaming them. Karl virus encrypts almost of files, including common as:
.xar, .xy3, .flv, .wbm, .odc, .gho, .db0, .rim, .wp6, .zip, .vdf, .hkdb, .ods, .jpe, .wm, .xxx, .srw, .xbplate, .kf, .rar, .vtf, .odt, .mef, .psd, .m2, .wire, .fsh, .iwi, .p7c, .wmf, .docm, .das, .cdr, .xlsm, .wp4, .webp, .orf, .syncdb, .mp4, .p7b, .wpb, .wmv, .xx, .pem, .dcr, .7z, .arw, .wps, .y, .wpg, .xmind, .xls, .xml, .vpp_pc, .wgz, .0, .cer, .slm, .webdoc, .xyp, .bay, .hplg, .wri, .doc, .t13, .crt, .ztmp, .raw, .ws, .arch00, .xdb, .avi, .jpg, .wn, .txt, .wdp, .itl, .vfs0, .litemod, .cfr, .sb, .re4, .xpm, .bik, .big, .srf, .crw, .xlgc, .wps, .zip, .x, .lrf, .upk, .xlk, .cr2, .ltx, .csv, .erf, .xf, .zabw, .wcf, .wotreplay, .xlsx, .mdb, .mov, .dba, .xlsx, .zi, .odm, .wbk, .wmo, .x3f, .menu, .wpa, .asset, .pef, .xmmap, .dxg, .lbf, .rb, .apk, .sie, .mlx, .blob, .wb2, .odp, .1, .sid, .rwl, .m3u, .wpd, .3dm, .ncf, .cas, .wsd, .pkpass, .ysp, .sav, .fos, .qic, .pdd, .layout, .w3x, .wsh, .3ds, .zdc, .wp5, .itdb, .wmv, .wpl, .pfx, .zw, .dazip, .xdl, .rw2, .ntl, .sidd, .accdb, .odb, .wbd, .iwd, .hkx, .r3d, .bar, .xls, .wdb, .wpd, .wp7, .mrwref, .ptx, .x3d, .dbf, .mpqge, .pst, .x3f, .xwp, .icxs, .mdbackup, .py, .dmp, .wpt, .rtf, .tax, wallet, .der, .forge, .z3d, .js, .xlsb, .mdf, .rgss3a, .snx, .itm, .png, .ibank, .mcmeta, .m4a, .yal, .indd, .ppt, .sql, .epk, .bkf, .pdf, .wbc, .vpk, .hvpl, .yml, .docx, .wpe, .mddata, .eps, .bc7, .bkp, .sr2, .sis, .wsc, .psk, .jpeg, .fpk, .bc6, .ai, .dwg, .vcf, .raf, .wmd, .ff, .xll, .esm, .wbmp, .wpw, .zif, .dng, .d3dbsp, .tor, .nrw, .3fr, .bsa, .wbz, .lvl, .1st, .svg, .xld, .2bp, .pptm, .t12, .xlsm, .p12, .css, .desc, .sidn
With the encryption work is complete, all locked files will now have the new ‘Karl’ extension appended to them. Karl ransomware virus drops a file named ‘_readme.txt’. This file contains a ransom note that is written in the English language. The ransom message directs victims to make payment through Bitcoins in exchange for the special code key needed to recover photos, documents and music.
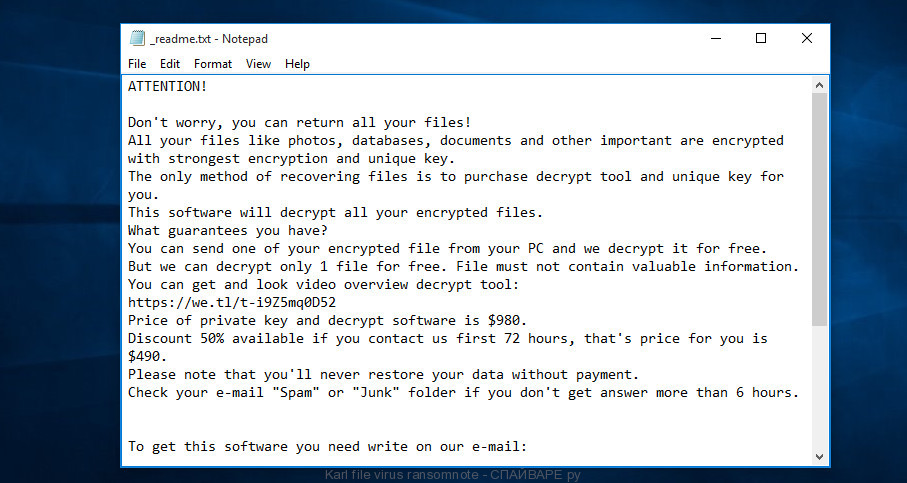
Karl file virus ransomnote
Threat Summary
| Name | Karl |
| Type | Crypto malware, Ransomware, File locker, Crypto virus, Filecoder |
| Encrypted files extension | Karl |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch |
| Ransom amount | $980 in Bitcoins |
| Symptoms | Your documents, photos and music fail to open. Files are encrypted with a Karl file extension. Your file directories contain a ‘ransom note’ file that is usually a .html, .jpg or .txt file. Desktop background is changed to the ransom note. |
| Distribution methods | Email attachments. Drive-by downloads from a compromised webpage. Social media, such as web-based instant messaging programs. Cybercriminals use misleading advertisements to distribute malicious software with no user interaction required. |
| Removal | To remove Karl ransomware use the removal guide |
| Decryption | To decrypt Karl ransomware use the steps |
If you came across this article, you were likely searching for a solution on how to delete Karl virus, which does not involve paying the money. The goal of this blog post is to provide you with the necessary instructions that can help you understand how delete ransomware and unlock documents, photos and music which have been locked.
Quick links
How to remove Karl file virus
Ransomware, spyware, trojans and worms can be difficult to delete manually. Do not try to delete this programs without the aid of malware removal utilities. In order to fully uninstall Karl crypto malware from your system, use professionally developed tools, such as Zemana, MalwareBytes Anti Malware and KVRT.
Remove Karl ransomware with Zemana
Zemana is a free tool that performs a scan of your PC system and displays if there are existing ransomware virus, spyware, adware, worms, trojans and other malware residing on your computer. If malware is detected, Zemana Anti-Malware (ZAM) can automatically remove it. Zemana does not conflict with other anti-malware and antivirus programs installed on your computer.
- Zemana Free can be downloaded from the following link. Save it on your Desktop.
Zemana Anti Malware download - After the downloading process is complete, close all apps and windows on your personal computer. Open a file location. Double-click on the icon that’s named Zemana.AntiMalware.Setup.
- Further, click Next button and follow the prompts.
- Once installation is done, click the “Scan” button to perform a system scan with this utility for the Karl crypto virus, other kinds of potential threats like malicious software and trojans. Depending on your personal computer, the scan can take anywhere from a few minutes to close to an hour. When a malicious software, adware or potentially unwanted programs are found, the number of the security threats will change accordingly.
- When Zemana completes the scan, you may check all threats detected on your computer. Review the results once the tool has done the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply click “Next”. When disinfection is finished, you may be prompted to restart your machine.
How to automatically uninstall Karl with MalwareBytes Anti Malware (MBAM)
We recommend using the MalwareBytes Anti Malware. You can download and install MalwareBytes AntiMalware to find and remove Karl ransomware from your PC. When installed and updated, this free malware remover automatically detects and removes all threats present on the system.
- Download MalwareBytes on your personal computer from the link below.
Malwarebytes Anti-Malware - At the download page, click on the Download button. Your web-browser will display the “Save as” dialog box. Please save it onto your Windows desktop.
- After the downloading process is complete, please close all software and open windows on your PC system. Double-click on the icon that’s named mb3-setup.
- This will run the “Setup wizard” of MalwareBytes onto your PC system. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes AntiMalware will run and open the main window.
- Further, click the “Scan Now” button to locate Karl ransomware virus, other malicious software, worms and trojans.
- When the system scan is done, the results are displayed in the scan report.
- All detected items will be marked. You can remove them all by simply press the “Quarantine Selected” button. Once the cleaning process is complete, you may be prompted to reboot the system.
- Close the Anti Malware and continue with the next step.
Video instruction, which reveals in detail the steps above.
Remove Karl ransomware virus from computer with KVRT
KVRT is a free removal utility that can be downloaded and use to remove ransomware viruss, adware software, malicious software, potentially unwanted software, toolbars and other threats from your system. You may run this tool to scan for threats even if you have an antivirus or any other security application.
- Download Kaspersky virus removal tool (KVRT) on your PC system by clicking on the link below.
Kaspersky virus removal tool - Once the downloading process is complete, double-click on the KVRT icon. Once initialization procedure is done, you will see the Kaspersky virus removal tool screen like below.
- Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next press Start scan button . Kaspersky virus removal tool tool will begin scanning the whole PC system to find out Karl crypto virus . This task can take some time, so please be patient.
- As the scanning ends, KVRT will display you the results. Next, you need to click on Continue to start a cleaning procedure.
How to decrypt Karl files
To decrypt Karl files, we recommend that you use the free decryptor created by Emsisoft. This decryptor will allow decrypting files that were encrypted with different versions of Stop (djvu) ransomware, including ‘Karl’ variant.
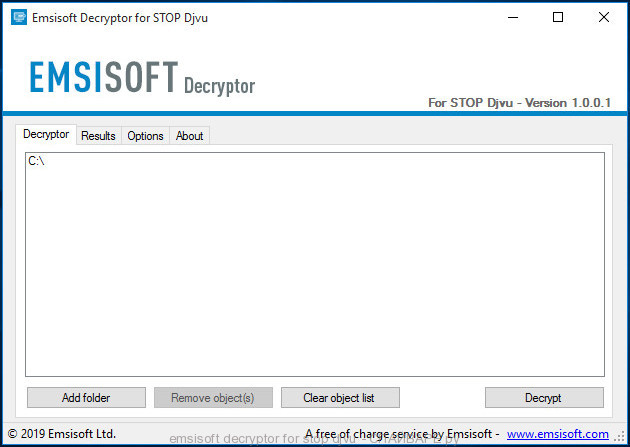
Emsisoft decryptor for stop djvu
How to use Stop (djvu) decryptor to decrypt Karl files
- Visit the page linked below to download Mosk decryptor
STOP Djvu decryptor - Scroll down to ‘New Djvu ransomware’ section.
- Download the ‘decrypt_STOPDjvu.exe’ file to your desktop.
- Run decrypt_STOPDjvu.exe
- Select the directory or drive where the encrypted files are located.
- Click the Decrypt button.
Unfortunately, it does not always help to decrypt files. If Stop (djvu) decryptor skips files without decrypting them, then we advise you to use alternative methods, which are listed below.
How to restore Karl files
Fortunately, there is little opportunity to restore documents, photos and music which have been encrypted by the Karl ransomware virus. Data recovery software can help you! Many victims of various viruses, using the steps described below, were able to recover their files. In our instructions, we recommend using only free and tested programs called PhotoRec and ShadowExplorer. The only thing we still want to tell you before you try to recover encrypted Karl files is to scan your personal computer for active malicious software. In our post we gave examples of which malicious software removal tools can identify and remove the Karl ransomware virus.
How to restore karl files using ShadowExplorer
To restore documents, photos, databases and other important files, that is, practically “decrypt karl files without a key,” we first recommend using a free program called ShadowExplorer. If you have not come across this program, then here is some information about it. It is a small utility that allows you to easily access copies of files that are created automatically by a standard OS function called Windows Previous Versions.
Download the program using the link that you can find below. We recommend that you save the downloaded file to your desktop, so you can easily find it after the download is complete.
When the program download is complete, you will see a file called ShadowExplorer-0.9-portable.zip. The utility is in the archive, so you need to unzip the archive before starting the program. Right-click on this file and select the option called Extract All. Now open folder ShadowExplorerPortable.
In the list of files, find the ShadowExplorerPortable program and run it.
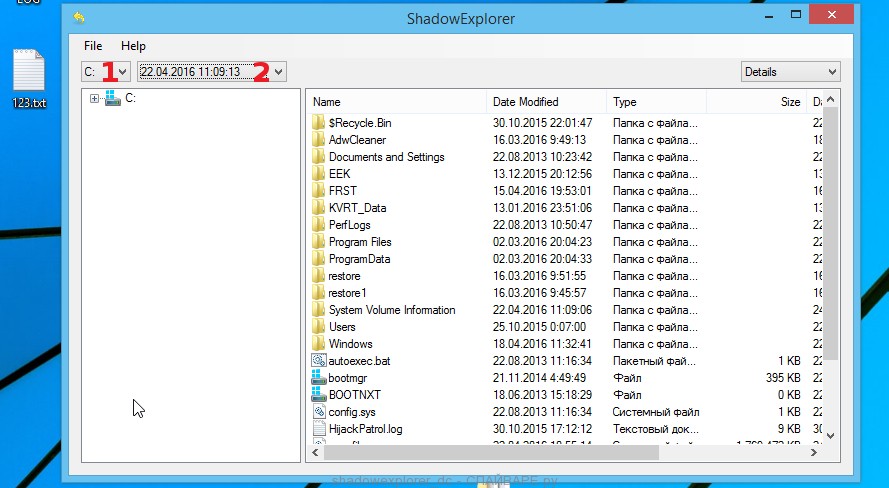
The main program window will open before you, as in the following example. The main window is divided into two parts – left and right. In the left part of the window, select the drive on which the encrypted files are located and select the date closest to the moment when the virus attacks your computer, encrypts the files and has changed the file extension to karl. In the right part of the window, select the file you want to restore, then right-click on it.
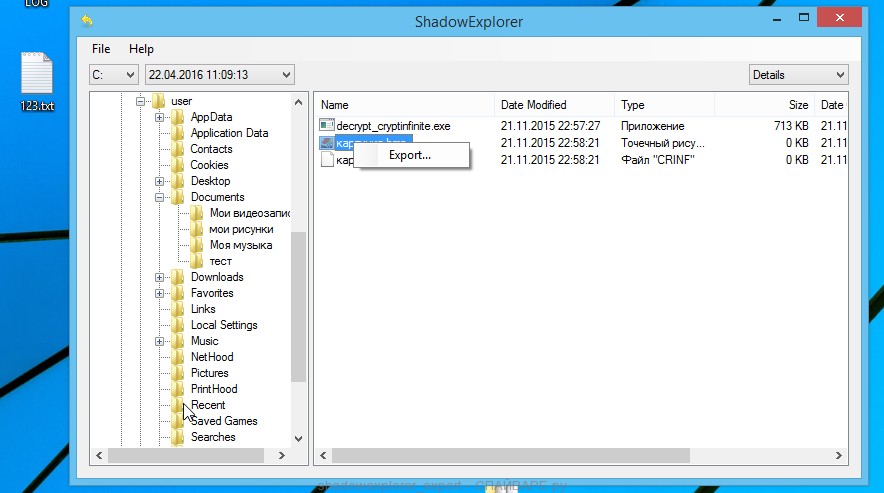
A small pop-up menu will open before you, select Export in it. In the next window, select the directory where the recovered files will be saved.
What else do I want to say about the process of recovering encrypted files using the ShadowExplorer tool. Unfortunately, very often ransomware disable the Windows Previous Versions function and delete all saved copies of files. Therefore, after starting the ShadowExplorer, you may find that it is impossible to recover files. In this case, use another method of recovering encrypted karl files, which is given below.
How to restore karl files using PhotoRec
Another way to recover encrypted karl files is the ability to use utilities designed to find and recover accidentally deleted and lost data. We recommend that you use the free PhotoRec tool. It is one of the best and has already helped readers of our site repeatedly recover encrypted files in a seemingly absolutely hopeless situation.
Before using the program, you need to download it. Use the link below.
When the file is downloaded, in the folder where you saved it you will see a file with the name ‘testdisk-7.0.win_.zip’. This file is the archive that contains the PhotoRec. To use the PhotoRec, this archive must be unzipped. Right-click on the file and select the item called Extract All. Open the folder with the name testdisk-7.0, you will see a list of files similar to the one below.
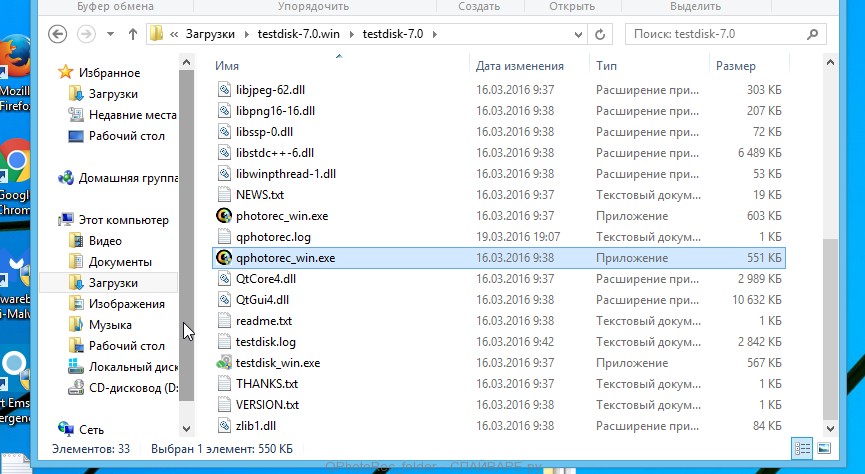
In the contents of the directory that opens, find the file with the name QPhotoRec_Win and run it. You will be shown a window similar to the one in the following figure. This is the main PhotoRec window.
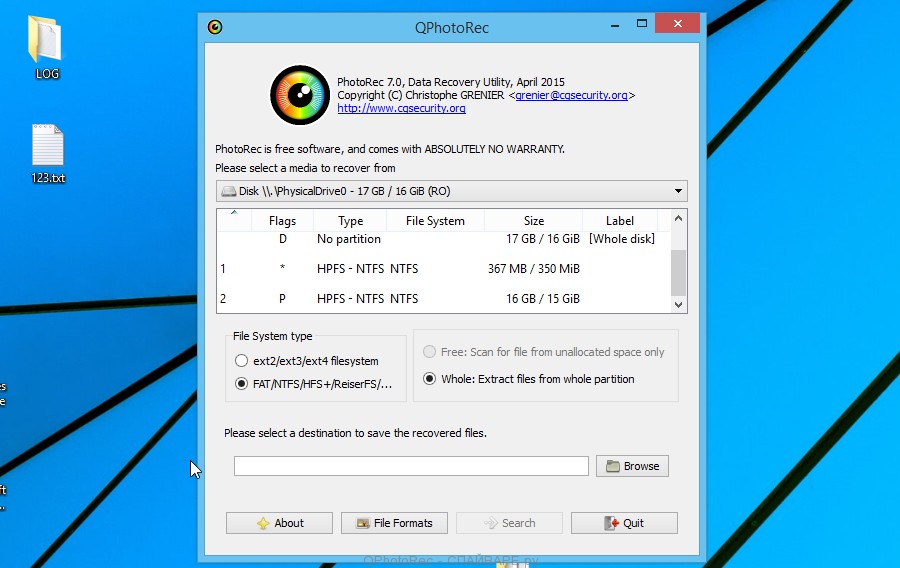
Here you need to select the physical disk and the disk partition (disk name) where the encrypted karl files are located. Note that in section ‘File System Type’, option ‘FAT/NTFS’ must be selected. Now select the folder where the recovered files will be written. We recommend using a partition or drive that does not contain encrypted files. It is better to use external media. It is very important! Since the PhotoRec restores files that were deleted by the Windows OS, if you restore them to the same drive on which you are trying to find them, a situation may occur when the Windows simply physically overwrites them and you can no longer recover such files.
Next, at the bottom of the window, click File Formats. A small window opens that lists the types of files that the PhotoRec can find and restore.
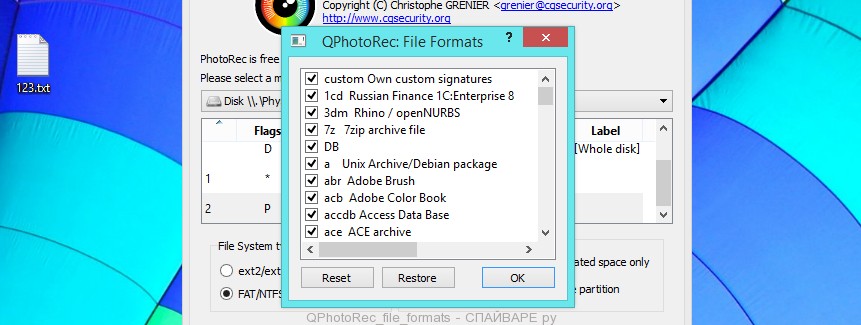
Leave only those file types that you need to recover selected. For example, if you want to restore images of ‘jpg’ format, then select the file type ‘jpg’. Having decided which files to recover, click OK button.
Having completed the steps listed above, you have made all the settings necessary to search and restore encrypted karl files. It remains only to click on the Search button. The process of searching and restoring files can take a very long time, be sure not to turn off the computer or restart it. During this process, the program will show the current search location (disk sector), how many and which files were found and restored.
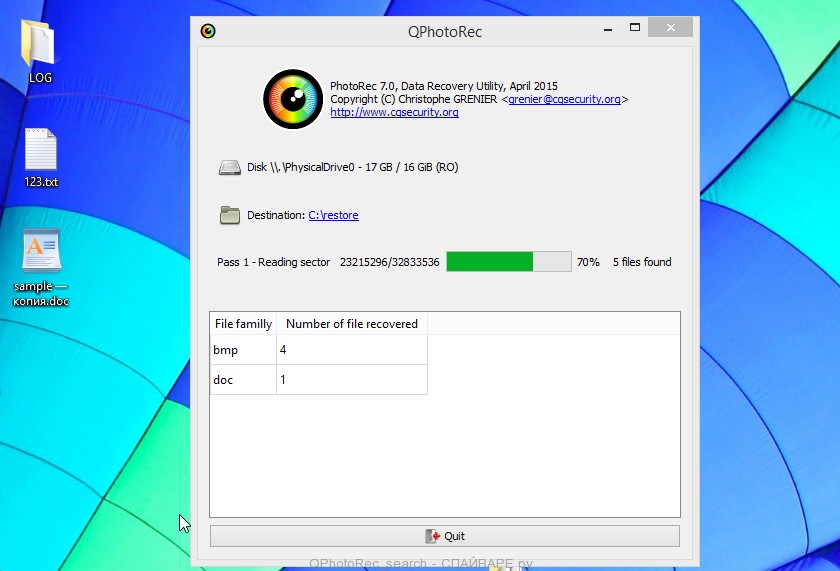
When the file recovery process is complete, click the Quit button. Then open the directory that you previously selected as the place where the recovered files will be written.
Here you will see one or more directories with the name recup_dir (recup_dir.1, recup_dir.2, …). Check these folder to find the files you need. The file name may not be restored, so to find what you need, use file sorting, as well as the standard Windows OS search by file contents.
I hope this information helped you remove Karl virus and restore the encrypted files. If you have any questions or you have information that will help readers of this article, then please add your comment below.